-
Wpa Password List Txt Download Skype카테고리 없음 2020. 2. 17. 14:48
It goes without saying that no device or network is completely secure. The white hat security researchers, as well as notorious hackers, keep on making continuous efforts to find a flaw in networks and take control of your devices. Your home or office WiFi network isn’t any exception. Compared to wired networks, WiFi networks pose an extra security challenge as their signals are accessible by the public.
Different security features like WPA2 can encrypt traffic, but there are techniques that have the power to tamper your security. So, it’s necessary to keep using different tools and methods to ensure your WiFi security. You can also read these and take care of the hacking attempts.Apart from Android, are there hacking tools for Windows, Linux, macOS, and iOS as well?Before introducing you to the world of WiFi hacker apps for Android, let me tell you that such tools do exist for other platforms as well. You can also choose a dedicated operating system for ethical hacking. Take a look:—— —Disclaimer: The WiFi hacking Android apps mentioned ahead in this list are for educational purposes only and one is expected to use them for testing their own security. Hacking or attempting to crack someone else’s WiFi security without permission is a criminal offense.
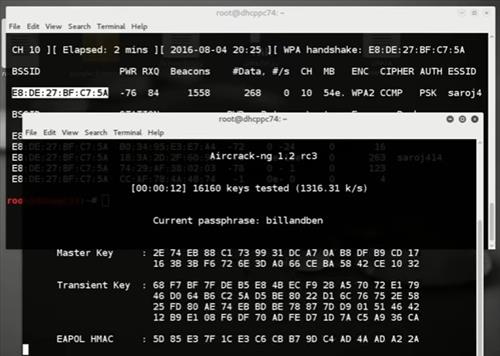
So, use these tools responsibly. 2017’s Top 12 WiFi Hacking Apps For AndroidNote: It’s a continuously updated list. I’ll be adding more tools to this list in future. Aircrack-ngFor testing network security and making sure that you’ve got tools to protect yourself–you need a real WiFi hacking app for Android. Apart from letting you learn the nuances of WiFi hacking, such an app will make sure that you’ve got yourself covered. Popular security tool aircrack-ng is one such tool, which has been ported to Android by many Android developers and security enthusiasts. Running aircrack-ng on Android isn’t much of an issue, but the difficult part is having a WiFi chipset that supports monitor mode. — Aircrack-ng ports:, 2.
WPA WPS TesterWPA WPS Tester Android app is one of the most popular WiFi password hacker tools, which was developed with an intention to scan the WiFi networks for vulnerabilities. This notorious hacking app is known for its ability to breaking the security. This app tests the connection to Access Points with WPS PIN, which are calculated using various algorithms like Zhao, Blink, Asus, Arris, etc. This app needs Android 4.0 and up for running.— 3. Kali Linux NethunterAlmost all of you must be knowing about Kali Linux, the. From their makers, Offensive Security, the Kali Linux Nethunter is the first open source Android penetration testing platform. Using this hacking Android app, you need to launch Kali’s Wifite tool to go ahead with the process.
Nethunter’s configuration interface lets you take care of the complex configuration files. Its custom kernel, which supports 802.11 wireless injection, makes Kali Nethunter a must have Android hacking tool.— 4. ZantiZanti, from the house of Zimperium, is a widely popular hacking app that allows the security managers to analyze the risk levels in a network. This easy to use mobile penetration toolkit can be used for WiFi network assessment and penetration. Its WiFi scanner shows the access points with known default key configuration in green. You can also use the app to kill connections to prevent the target to access any website or server. By mirroring such methods used by cyber attackers, you can identify the holes in your network and make amends.—5.
ReaverReaver for Android, also called short RfA, is a WiFi password hacker app that’s a simple-to-use Reaver-GUI for Android smartphones. Shipping with the monitor-mode support that can be activated and deactivated anytime, Reaver detects WPS-enabled wireless routers on its own.
With its GUI, all the Reaver settings are available. This WiFi hacking app launches a brute force attack against WPS registrar PINs and recovers the WPA/WPA2 passphrases. Tested on a wide variety of devices, Reaver is able to get the target AP’s plain text WPA/WPA2 passphrase in 2-5 hours. Last but not the least, Reaver for Android also supports external scripts. WiFi Analyzer (a prank app)WiFi Analyzer isn’t exactly a WiFi hacker app for Android, it’s a prank app.
I thought it would be a good idea to end this list of WiFi hacking apps with an app that lets you pretend as if you’ve broken into your friend’s WiFi and gained access. It has a very professional look and a WiFi scanner that detects all WiFi hotspots nearly.
Password Txt Free Download
So, if you’re simply interested in fooling your friends, give this a try.— Other notable Android WiFi hacking apps:Apart from the above-mentioned Android applications for penetration testing and security analysis, there exists an overabundance of other apps that you can download on your device and use. Some of such notable Android WiFi hacking tools are:. Shark for Root. Fing Networks Tools. Router Keygen. WiFi Inspect.

ArpspoofSo, did you find our list of best apps to hack WiFi network useful? Give them a try and improve ethical hacking skills.
With finally launching this week, we’re going to see a slate of articles discussing the OS’s new features and capabilities. Some of these are significant upgrades compared with what came before, while others could be potentially controversial. One new option, brought over from Windows Phone 8.1, is called WiFi Sense, but its debut on the desktop could be controversial given what the feature does.WiFi Sense will automatically connect you to detected crowdsourced WiFi networks, acquire network information and provide “additional info” to networks that require it (it’s not clear exactly what constitutes additional info), and can be used to automatically share your WiFi password with your contacts on Facebook, Skype, and Outlook.
Wpa Password List
That last feature is the potentially controversial one. WiFi Sense is enabled by default in; if you choose “Express Settings,” Microsoft enables the option and allows your device to acquire WiFi passwords from friends and shares your password with the same group of people. If you choose to leave the function enabled (or turn it on manually, as shown below), it will request permission to connect to Outlook, Skype, and Facebook on your behalf. Other users on your friends list who also run Windows 10 will have their contact information shared with you as well, assuming they also enable the feature.Microsoft claims that this feature improves security and reduces frustration. Now, instead of painstakingly spelling or writing down passwords for guests or friends, they can automatically acquire them as soon as they come in-range of your home network. The company’s states.
“When you share Wi-Fi network access with Facebook friends, Outlook.com contacts, or Skype contacts, they’ll be connected to the password-protected Wi-Fi networks that you choose to share and get Internet access when they’re in range of the networks (if they use Wi-Fi Sense). Likewise, you’ll be connected to Wi-Fi networks that they share for Internet access too. Remember, you don’t get to see Wi-Fi network passwords, and you both get Internet access only.
They won’t have access to other computers, devices, or files stored on your home network, and you won’t have access to these things on their network.”In theory, Microsoft could be right, but the company is also creating a de facto database of WiFi information. Elsewhere in the FAQ, Microsoft notes that if you choose to share this information, it’s sent via an encrypted link to Microsoft, who stores the data on their own servers (again in encrypted format). This isn’t as foolproof as it might have once seemed; we’ve covered multiple bugs related to Internet encryption standards in the past nine months. The other concern we have with WiFi Sense is that the feature has no granularity beyond the service level.
I can choose to share or not-share information with Facebook, Outlook, or Skype, but that’s it. If you share your network information with anyone on your Facebook friends list, you’re sharing it with everyone on your Facebook friends list.
That’s something Microsoft really ought to have addressed when it brought the feature over from Windows Phone; just because I want to share this kind of data with some people doesn’t mean I want to share it with everyone. The continued degradation of privacyThe risk of exposing your network connection to ne’er-do-wells on Facebook or Outlook.com is small, but it’s not zero. The bigger issue I want to highlight, though, is how features like this indirectly erode the concept of user privacy and the perceived need for good security practices. This is something we’ve talked about before, but it’s not just an Apple or a Microsoft problem.On the one hand, we tell people that they need to secure their data with strong passwords while research shows how passwords are trivial to hack — even many strong passwords can be cracked fairly easily. Services like LastPass promise to offer protection, only to fall prey to hacks in turn. When companies get hacked, whether its Target or LastPass, the consequences of these failures are often trivial. Even Lenovo, which installed one of the most to ever ship on modern PCs, appears to have come through its Superfish debacle largely unscathed.
This tension is at the heart of all security systems, not merely the online ones. If designing secure systems is difficult, designing secure systems that are both fast and easy-to-use is borderline impossible. Nonetheless, online companies often encourage users to share information that proper security practices say ought not be shared, while the consequences of security breaches for the companies that breach them are so small, it sends the message that hey — privacy and security aren’t really things you need to care about. And it just so happens that this relatively lax attitude towards privacy underwrites the business model of multi-billion dollar corporations, many of whom seek ever-more lenient rules on what they can and cannot do with your personal information.On a practical level, the risks from WiFi Sense are small. But from a best-practices security standpoint, it’s far from a great idea.